Proactive Cyber Defense for a Rapidly Evolving Threat Landscape
Cyber threats are evolving faster than ever, and traditional security measures are no longer enough to protect against sophisticated cyberattacks. Organizations face ransomware, zero-day exploits, insider threats, data breaches, and nation-state cyber warfare-all requiring a proactive, intelligence-driven approach to cybersecurity. We deliver comprehensive cybersecurity solutions that empower organizations to detect, prevent, and respond to threats before they impact business operations. Our zero-trust security frameworks, AI-powered threat detection, compliance solutions, and incident response strategies ensure maximum protection for your critical assets. With expertise in NIST, CISA, MITRE ATT&CK, Zero Trust Architecture, SIEM, XDR, and compliance standards such as HIPAA, NIST, SOC 2, FedRAMP, ISO 27001, and PCI DSS, AASI provides the highest level of cyber resilience and risk management.
Why Choose AASI for Cybersecurity?
- Advanced Threat Intelligence & AI-Powered Security – Stay ahead of cyber threats with real-time AI-based anomaly detection and predictive analytics.
- Zero Trust Security Architecture – Implement end-to-end identity verification, least privilege access control, and continuous monitoring.
- 24/7 SOC & Incident Response – Our Security Operations Center (SOC) provides round-the-clock threat monitoring, rapid response, and digital forensics.
- Cloud Security & Compliance – Secure your AWS, Azure, and Google Cloud environments with cloud-native security controls and compliance automation.
- Network Security & Endpoint Protection – Next-gen firewalls, intrusion detection/prevention (IDS/IPS), EDR, and MDR solutions for real-time threat mitigation.
- Cyber Risk & Compliance Management – Align with NIST, CISA, ISO 27001, HIPAA, FedRAMP, PCI DSS, GDPR, and SOC 2 regulations.
AASI’s Cybersecurity Framework
Our cybersecurity methodology is built on proactive defense, threat intelligence, compliance, and AI-driven automation.
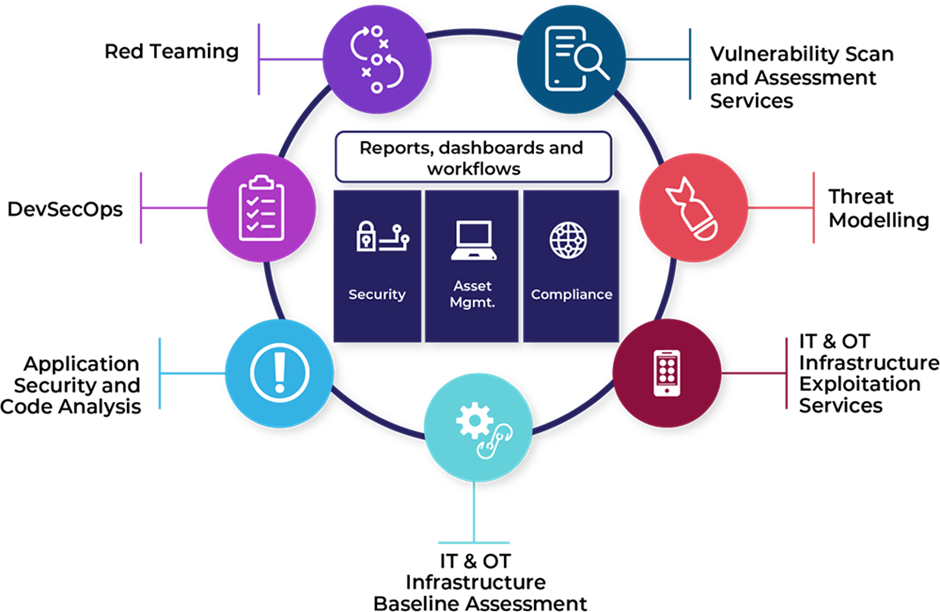
- Cyber Risk Assessment & Security Posture Evaluation: We conduct in-depth cyber risk assessments to identify vulnerabilities through penetration testing, red teaming, and attack surface analysis. Our approach ensures a thorough evaluation of compliance gaps against industry standards such as NIST CSF and MITRE ATT&CK, as well as regulatory mandates. By developing a customized security strategy tailored to specific business objectives and threat landscapes, we help organizations strengthen their overall security posture.
- Threat Detection, Prevention & Incident Response: We deploy AI-powered Security Information & Event Management (SIEM) solutions for real-time anomaly detection and proactive threat management. Our advanced security framework includes Endpoint Detection & Response (EDR) and Managed Detection & Response (MDR) solutions to provide continuous monitoring and rapid threat mitigation. With a dedicated 24/7 Security Operations Center (SOC), we ensure proactive threat hunting, rapid incident response, and minimized attack impact.
- Identity & Access Management (IAM) & Zero Trust Implementation: We implement robust identity and access management strategies, enforcing multi-factor authentication (MFA), least privilege access controls (RBAC & ABAC), and passwordless authentication for enhanced security. Our Zero Trust Network Access (ZTNA) model prevents lateral movement of threats, ensuring secure and controlled access. Additionally, we automate identity lifecycle management to streamline secure user provisioning and deprovisioning.
- Cloud Security & DevSecOps Integration: We secure cloud environments across AWS, Azure, and GCP using Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platforms (CWPP). By embedding security into CI/CD pipelines with DevSecOps best practices, we ensure secure and compliant software development. Our encryption strategies safeguard data at rest, in transit, and in use with robust cryptographic controls, preventing unauthorized access and data breaches.
- Cyber Resilience, Compliance & Governance: We establish cyber resilience strategies that integrate AI-driven risk management and disaster recovery planning, ensuring business continuity in the face of cyber threats. Our approach ensures compliance with industry regulations, including NIST, HIPAA, PCI DSS, GDPR, SOC 2, and ISO 27001. Additionally, we provide automated compliance reporting and governance frameworks to help organizations maintain security, transparency, and regulatory alignment.
Industry-Specific Cybersecurity Solutions
AASI delivers customized cybersecurity services tailored to the unique security and compliance needs of each industry.
- Financial Services & Banking – AI-driven fraud detection, real-time threat monitoring, PCI DSS compliance.
- Healthcare & Life Sciences – HIPAA-compliant data protection, medical device security, and AI-powered patient privacy solutions.
- Government & Public Sector – FedRAMP-certified cloud security, CISA-compliant frameworks, and cybersecurity modernization.
- Retail & eCommerce – Secure online transactions, fraud prevention, and identity verification solutions.
- Manufacturing & Critical Infrastructure – Industrial Control System (ICS) and SCADA security, OT/IT network segmentation.
Success Stories: Real-World Cybersecurity Excellence
Stopping a Ransomware Attack for a Fortune 500 Financial Institution
“AASI’s XDR & AI-powered threat intelligence platform detected and neutralized a ransomware attack before it could encrypt critical banking data, preventing a multi-million-dollar loss.”
Strengthening Cyber Resilience for a National Healthcare Provider
“Our Zero Trust security framework, IAM solutions, and AI-based anomaly detection enabled a leading healthcare provider to secure patient data, meet HIPAA compliance, and prevent insider threats.”
Securing a Multi-Cloud Environment for a Global Retailer
“AASI implemented cloud-native security controls, CSPM, and real-time threat analytics to protect a hybrid AWS-Azure-GCP infrastructure supporting millions of transactions daily.”
Contact us today to schedule a free cybersecurity consultation and take control of your security posture!

